Network protocol: What is a network protocol and how it works?
By having a great diversity of devices interconnected in Industry 4.0, communication is a priority among equipment, intending to receive, emit, analyze, distribute or even just display data and information for processes. But these wouldn’t be possible without the network protocols.
In the following paragraphs, we will discuss network protocols, what they are, the classification of network protocols and how they work, in general.
Index
- What is a network protocol?
- Network protocol’s history
- How do network protocols work?
- OSI and TCP/IP models in network protocols
- Network protocol types
What is a network protocol?
A network protocol is a communication standard; this means it contains the necessary information and rules about how computers exchange data with each other. Different types of interaction are required for many tasks, such as the simple exchanges of messages.
Thus, each protocol assumes a specific task in the context that is required, covering sectors such as industrial or business. The network protocols are developed by entities, organizations, or people who work in industry, research institutes and more.
After that, they get published and accepted in international conferences to establish communication standards such as the ISO (International Standard Organization), and the OSI (Open Systems Interconnect) architecture, to mention some examples. Later we will see the characteristics of this model and another one, TCP/IP. In general, network protocols carry out the following tasks:
- Establish a reliable connection between the teams involved in the communication.
- Directly sent data packets to the correct recipient.
- If the packets do not arrive, the protocol ensures they are forwarded.
- Error-free transmission of information packets.
- Organization and merging of incoming data packets.
- Transmit encrypted data, so it can’t be read by third.
For this reason, network protocols are defined as guidelines, norms or rules by which a user communicates through the Internet (network or set of local networks distributed through the world) or Intranet (that works like the Internet but is for computers set for a specific user’s group).
Both ends of the communication channel follow these rules for proper information exchange. It also has the task of avoiding manipulation by third parties, whose environments are also known as cybersecurity.
There are many types: IP or Internet Protocols, for example, this is digital communication basis as we know it. This protocol allows us to maintain digital communication, as we all do now. Network protocols such as IMAP (Internet Message Access Protocol), SMTP (Simple Mail Transfer Protocol) and POP3 (Post Office Protocol) are also used in daily life in the industry so that, within the same installation and send emails.
In addition, digital communication is essential for people to maintain their usual lifestyle. Thus, it could be serious if all the world’s wireless network processes fail at some point.
Therefore, various systems were created to enable successful communication, as well as network protocols because they play an important role in optimizing the development of computer communications. These protocols are classified in various bases such as some maps for the transport layer, others for network layers protocols, and in this way, they move between each one of them.
However, we will leave that for later and now, we will continue with a bit of historical context and how they arose.
Network protocols history
To talk about the history of network protocols, go back to the implication derived between the United States and the extinct USSR to establish a hegemonic power in science and military technology.
In 1957, the American organization ARPA (Advanced Research Projects Agency) created ARPANET, the Internet predecessor. Therefore, during the decade of the sixties, an essential part of the protocols that exist today were developed so the purpose, a common language had to be used regardless of the region where it was being used.
The protocol used at that time in the machines connected to the ARPANET was called NCP (Network Control Protocol), but over time it gave way to another advanced protocol: TCP/IP.
It is worth mentioning that this protocol is made up from other different, highlighting the two that prevail in its name, TCP (Transmission Control Protocol) and IP (Internet Protocol).
How do network protocols work?
The network protocol’s operation works according to the type in question. To do this, we exemplify the search for IP, and, in addition, we will delve into the network protocol layers of two different models to understand how they act and connect.
The simplest example is when we search for something in our browsers. The client uses his system browser from which he sends a request on the Internet, once he visits that URL, the call is routed through the channel to the DNS server and the IP is looked up. The DNS installs a cache, a high-speed data storage layer that collects transient information, so that future requests are returned to an IP address. After IP resolution, the client’s requirements arrive at that host’s web server.
OSI and TCP/IP models in network protocols
If we want to define network protocols, there are two types of layered models in which they are found:
-
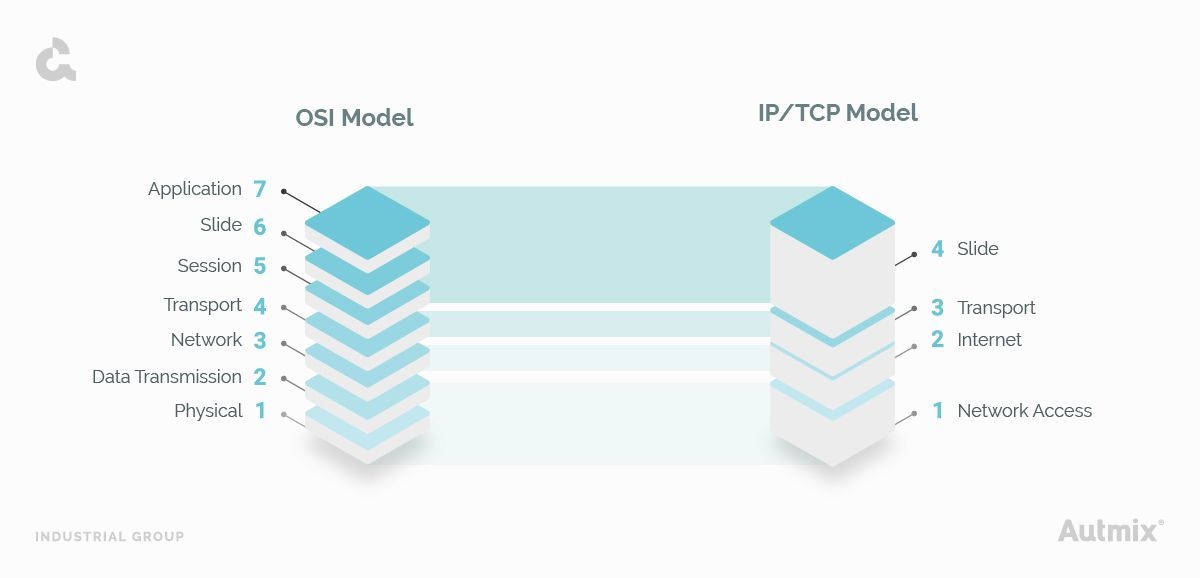
OSI Model: a regulatory system made up of seven levels that define the interconnection of systems in the different phases, also known as layers, through to travel from one device to another in a telecommunications network.
-
TCP/IP model: with the TCP protocol, information is divided into small “information packets” that travel independently and are assembled again at the end of the process, while IP oversees finding the destination route.
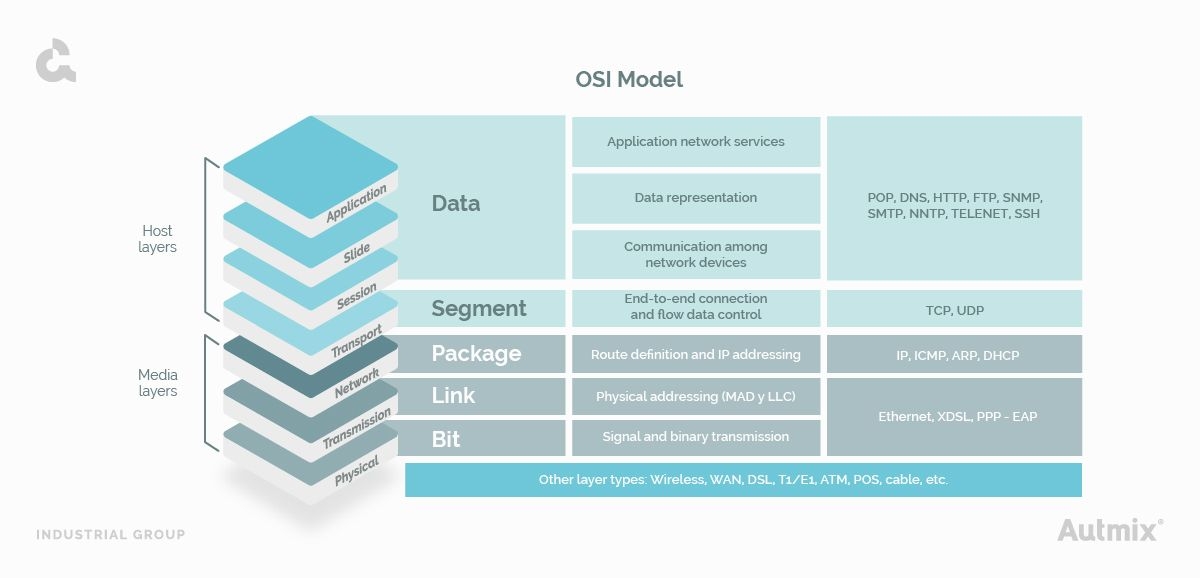
OSI Model is made by 7 layers, which fulfill the homonymous functions:
- Application layer
- Slide
- Session layer
- Transport layer
- Network layer
- Data Transmission level
- Physical layer
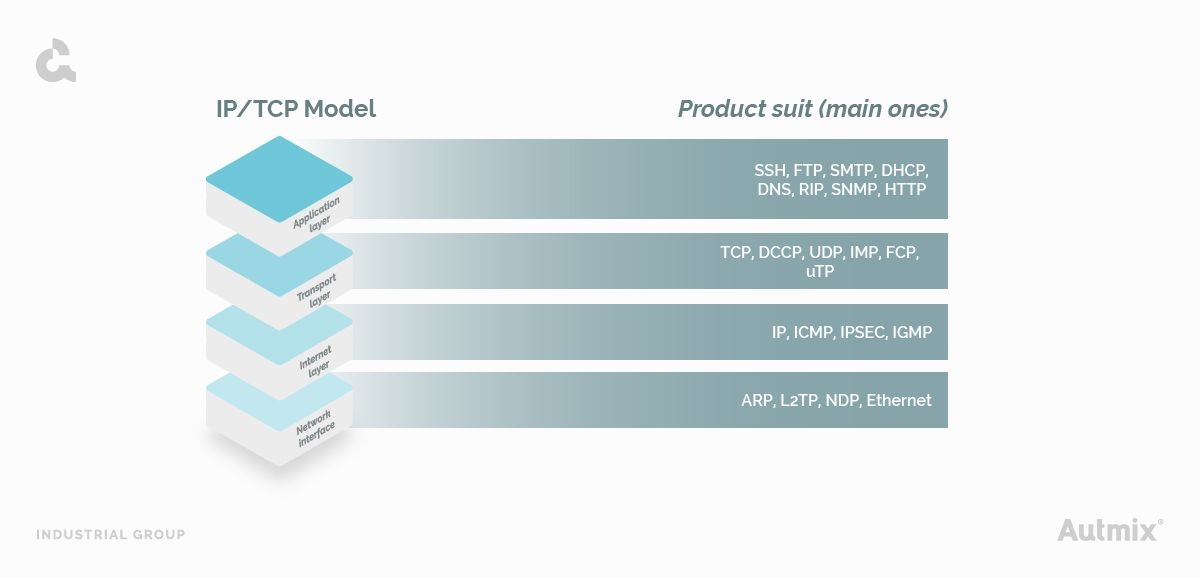
Instead, TCP/IP model, unlike the OSI model, contains only four layers that perform the following tasks:
- Application layer
- Transport layer
- Internet
- Network access
It is worth mentioning, specifically, the particularities of the IP model to understand how it works with TCP.
In this case, it is necessary to explain what the IP is. When users send or receive data from a device, the data is divided into packets with two IP addresses: one for the sender and another for the recipient. After the sender sends the packet, it goes to a gateway. Like a post office, this forwarding the package to the correct address. Thus, the packets are sent through paths that finally reach their destination.
As anticipated in the historical section, IP is combined with TCO to form TCP/IP. Both form Internet protocols. The division of labor works like this: IP sends packets to their destination, and TCP puts them in the correct order. This is necessary because IP sometime sends the data set out of order to ensure that the data travels the fastest route.
Having explained the above, we can identify the previously mentioned layers with the following functions.
- Application layer: owns the user data and manages the encryption mechanisms.
- Transport layer: supports communication between end devices.
- Internet layer: provides logical addressing.
- Network layer: controls hardware devices such as routers.
- Data link layer: responsible for MAC addressing and communication with the physical layer.
- Physical layer: carries everything on the wired layer.
Now we will review the types of network protocols.
Network protocol types
- IPv6: Refers to Internet Protocol Version 6, it's the future addressing format. Once IPv4 addresses are exhausted and public IPs are moved to version 6, this will allow unique combinations in which addressing can be done, and, therefore, will represent many machines connected to the Internet.
- IPV4: In IPv4 addressing, there are public and private IPs. The private IP can be accessed on the network and the public IP can be accessed over the Internet.
TCP/IP based protocols are divided into the following areas: web, file transfer, email, management, and media.
Web protocols
HTTP: means Hypertext Transfer Protocol. The format of the messages, their transmission and the associated web actions on the client and server side are managed by this protocol. The WWW (World Wide Web) uses it. It runs on port 80.
HTTPS: stands for Hyper Text Transfer Protocol Secure, so it is just an improvement away from the local host.
TLS: means Transport Layer Security. This cryptographic protocol provides end-to-end communication security over networks commonly used in transactions. The fight guarantees protection against counterfeiting, the prevention of data leaks, etc.
SSL: also known as Secure Sockets Layer, establishes an encrypted connection between the browser and the server, the web server requires an SSL certificate. Public and private keys are created cryptographically.
File transfer protocols
FTP: File Transfer Protocol is used for file transfer between client and server on a computer network.
TFTP: refers to a standard trivial file and put it on a remote host. LAN nodes are used.
SFTP: the SSH file transfer protocol provides a secure connection for a transferring file and traversing the file system in local and remote systems.
FTPS: it is a secure file transfer protocol. TLS and SSL support are added here. A secure shell-based protocol is not used.
SMB: Server Message Block, used by Windows, allows computers on the same network to share files.
NFS: Network File System is a distributed file system commonly used on UNIX to access files between email protocols.
SMTP: Simple Mail Transfer Protocol is a push protocol for sending an email and Post Office Protocol or Internet Message Access Protocol is used to retrieve it at the receiving end. It is implemented at the application level.
Management protocols
Telnet: applied on the Internet and LÑAN for two-way text communication. A virtual terminal connection is needed for this purpose.
SSH: is a secure shell-based remote login from one computer to another. This allows us to take care of authentication and security.
SNMP: Simple Network Management Protocol, used to collect and organize information about network devices and exchange information to devices on the network and to exchange information.
Media protocols
RTP: Real-time transport, used for audio and video communication over the network.
RTSP: Real Time Streaming Protocol, is a streaming protocol that enables media sessions between endpoints.
Thus, we talk about what network protocols are for IT and how they are used. Later we will explain the different standards in industrial procedures. Here at Autmix, we have experts in communications and network protocols to support you in using the best one based on your company’s needs. Contact us!
Reduce your operating costs
I want to be contacted